March 21, 2022 / By Securium Solutions
What is Directory Brute Forcing?
Directory Brute Forcing (also known as directory busting or directory enumeration) is the process of attempting to find hidden or unprotected directories and files on a web server by using a tool or script. It’s often used in web application security testing to identify potential vulnerabilities.
There are several tools available for directory enumeration
- DirBuster
DirBuster is an open-source web application security testing tool. It’s designed to discover hidden directories and files on a web server. It works by launching a dictionary-based attack against a web server, where it will try to guess directory and file names using a list of common names and extensions.
DirBuster can be useful for web application penetration testing, where it can help identify potential vulnerabilities such as exposed sensitive files or directories that could be accessed without proper authorization. It can also be used to discover hidden content that may not be easily accessible from a website’s navigation.
DirBuster can be downloaded and used on Windows, Linux, and macOS operating systems. It comes pre-installed in kali or can be manual via “sudo apt install dirb” command.
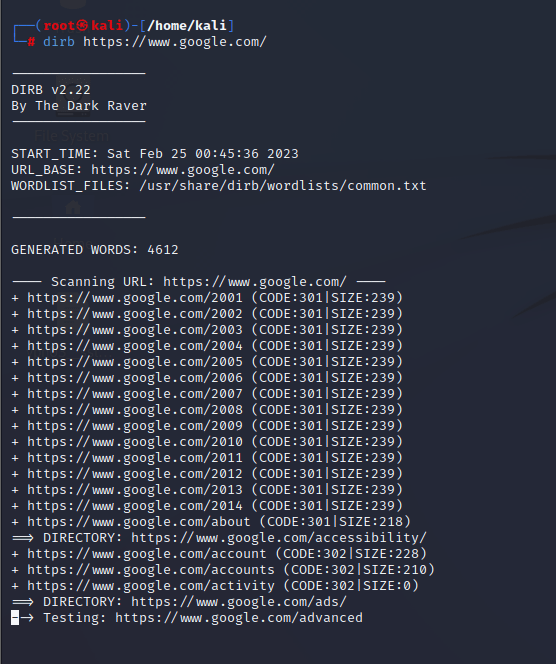
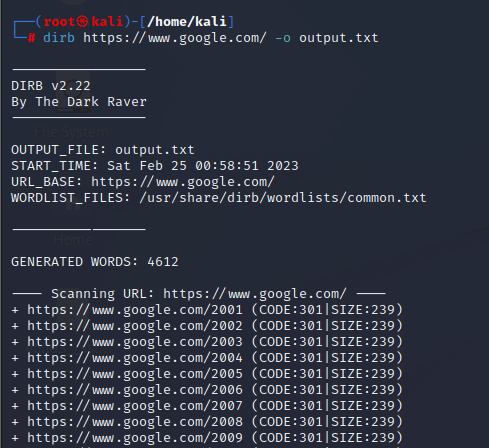
To scan for hidden directories using dirb can be achieved by using the command:
dirb <url> or dirb http://<ip>
Knowing about the commands and their usage of dirb tool, can be achieved by using the “man” command which is the acronym for manual.

Filters in DirBuster
Dirb offers multiple filters to advance the scanning result.
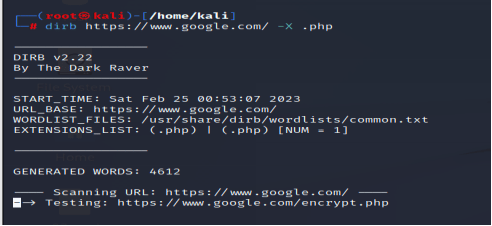
(1) To search for URLs those have only .php extensions in it
By using the –X flag during scanning, it’ll only display the hidden directory that has .php extensions in it.
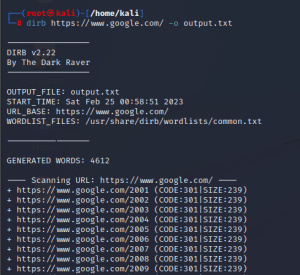
(2) To Save the output in a text file
By using the –o <filename> flag, it’ll save the scanned result in a text file.
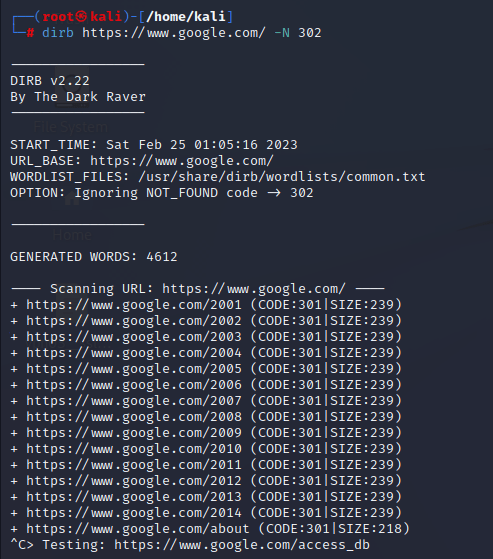
(3) To ignore specific response code
While scanning the hidden directory, dirb also displays which are forbidden and some which are redirected to other pages, to ignore those response results dirb offer –N <response code>
flag.
- Gobuster
Gobuster is also an open-source web application security testing tool. It is used for directory and DNS subdomain brute-forcing. It’s similar to DirBuster and performs similar functions, but it’s known for its speed and efficiency.
Gobuster can be used on various operating systems, including Windows, Linux, and macOS.
It comes pre-installed in kali linux or can be installed manually, using
apt install gobuster (root privileges).
To get to know about the commands and their usage of gobuster tool, can be achieved by using the “gobuster -h” or “ gobuster –help”.
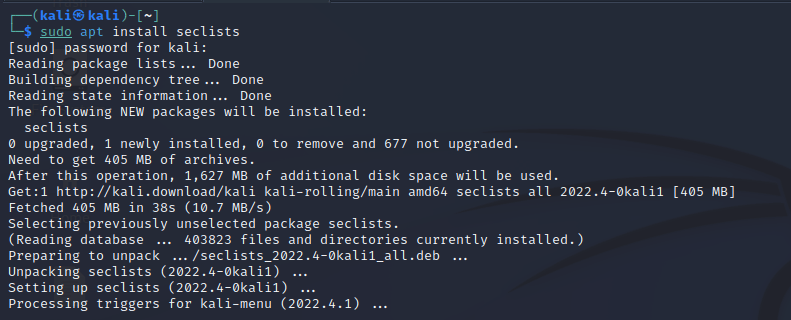
To use gobuster effectively, it’s required to install seclists that contain various wordlists which are used to provide a list of words that the tool will use to perform directory and subdomain brute-forcing. These wordlists contain common directory and file names, as well as subdomain names that may be used by websites.
It can be installed using the command: sudo apt install seclists.
Gobuster offers two types of modes:
- DNS mode: DNS mode in gobuster is used for scanning the hidden subdomain of an url.
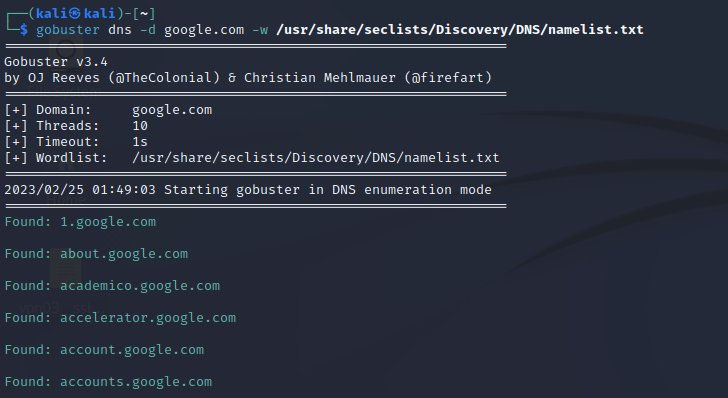
It can be achieved by using :
Command: go buster dns –d <domain-name>.com -w /usr/share/seclists/Discovery/DNS/namelist.txt
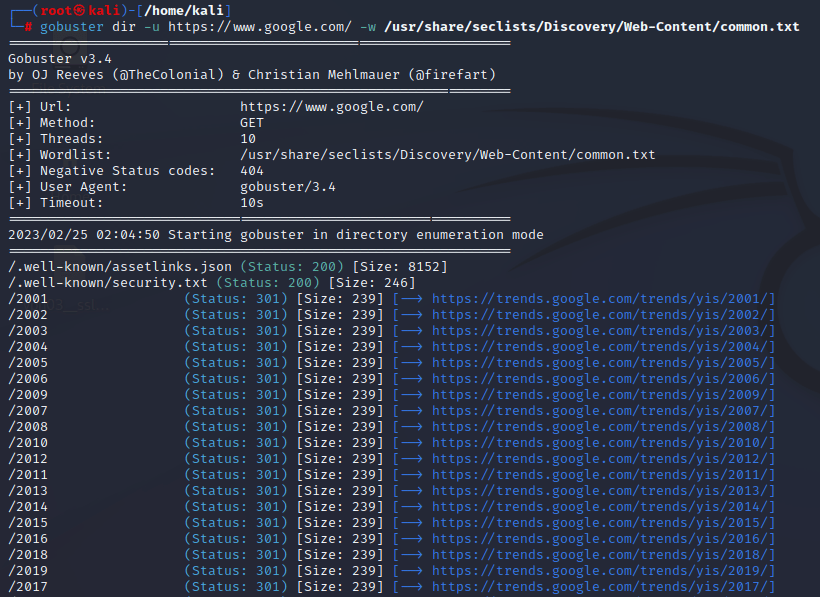
- Dir Mode
The “dir” mode is used for brute-forcing directories on a web server. It can be a useful tool for identifying potential security vulnerabilities in web applications by uncovering hidden or unprotected directories.
The Command for dir mode: gobuster dir –u http://<url> -w /usr/share/seclists/Discovery/web-content/common.txt
Gobuster comes with several built-in wordlists that users can choose from, including:
- txt– a list of common file and directory names
- txt– a larger list of common directory and file names
- txt– a medium-sized list of common directory and file names
- txt– a small list of common directory and file names
- raft-large-words.txt– a list of common words used in the English language
- raft-medium-words.txt– a smaller list of common words used in English language
Users can also create custom wordlists to use with Gobuster, which can be useful in certain situations where a specific type of content or naming convention is used by the target website.
Author
Abhi Gaur
(Cyber Security Intern)